What is Email Phishing? Examples of Phishing Emails
Phishing Email Definition. How to spot a phishing email? Examples of Phishing Emails and how to protect yourself from email phishing.

Attackers are always on the lookout for new victims. With the high penetration rate and adoption of the internet and internet-enabled devices, the number of victims is on the rise. Whereas there are many types of attacks and hacks, most of them require sophisticated tools and scripting knowledge to launch, let alone operate and disguise. However, there is one where anyone with an internet connection can launch - email phishing.
Email Phishing Meaning
Email phishing (pronounced /fishing/) is an example of social engineering attack where malicious actors (attackers) send out emails designed to appear legitimate to trick people into falling for a scam, con, or cyberattack. Through phishing, attackers are always targeting to collect your personal information, including credit card numbers, login information, and other PII (personal identifiable information).
Why is Email Phishing Common and Widespread?
-
In a 2022 report, as of 2022, there were over 4.26 billion email users in the world and this number was expected to grow with over 100 million each year. Gmail (Email services by Google) alone had over 1.5 billion email users, with each user having an average of 1.7 email accounts.
-
Email service providers such as Gmail(Google), Outlook(Microsoft), iCloud Mail (Apple), and others support tens of languages across the world. For instance, Gmail alone supports over 105 languages worldwide.
-
Email has become a central means of communication between peers, businesses, and even businesses to individuals.
-
Almost all websites require an email for communication and/or log in. That means that through your email address, you can access your bank's services, social media account, cloud storage, e-commerce website, and even your local pet vet's information and appointment-booking website.
Now you can have an understanding of why attackers find email phishing the most seamless and easiest way to launch scams and attacks. With a single crafted email and a single click, an attacker or an email scammer can send out thousands, if not millions, of emails every single day. If it is estimated that for every 1000 phishing emails sent, 1 is successful.
In a 2023 report, over 3.4 billion phishing emails are sent out every day. That means, there are 3.4 billion hacks attempted every single day through emails. If over 1% of email phishing scams and hacks are successful, you can understand why it is regarded as a billion-dollar enterprise.
If you are reading this, 99.9% chance you have at least one active email address. So, how can you avoid being in the 1% success email phishing scam statistic? Here is the good news about protecting yourself from phishing scams - you do not need to have special IT skills like those of a cyber security expert. All you need to have is a keen eye on the small details of any emails in your inbox folder and a more strict attitude to emails in your SPAM folder. Although there are other tools and techniques you can employ to spot phishing emails, let's first focus on the easiest and cheapest to implement - more like a DIY (do-it-yourself).
How to Spot a Phishing Email
You see, no phishing email is perfect, although some are well crafted more so if the attacker has IT skills and uses hacking tools. However, 90% of the daily phishing emails we receive are sprinkled with breadcrumbs that you can recognize as red flags.
Here are a few:
1. Email Has Been Flagged as Spam
Well, this is easy to spot. Email providers help to spot fake and phishing emails from senders before it hits your mail inbox by using complex and robust tools such as email filters. Whereas some emails are completely blocked from being received, you might receive others with a spam label or in your spam folder. Once an email is marked as spam, most email providers will disable links and attachments and let you decide if the email is legitimate.
In some cases, we have seen legitimate emails flagged as spam and placed in the spam folder. If you are not sure about an email in your spam folder, it is best to leave it there until you can ascertain that it is legitimate or delete it entirely if you can't confirm its authenticity. In other cases, phishing emails have not been flagged, and in such situations, extra caution is recommended when interacting with emails.
2. Uses a Public Email Domain (Alleges to be From an Organization)
Let's set up a scenario:
You are a loyal customer of ABZ Bank. Your bank has a website, , where people can visit for more information, and clients log in to check their balances and even transact from their accounts. Since you signed up for newsletters from the bank and the bank has been sending account notifications to your email, it uses the email address customer.support@abz.com. However, you have a new email from .
Let's pause for a moment...
Without going into the body of the email, there is information available to you. You can use this information to see an email address in addition to the name, the subject line, the address that the email was sent to (or all if the sender used the carbon copy, the CC option), security encryption used, and more. In Gmail, you can follow the procedure below:
1) In the email body, click the down arrow in the email information box:

2. Analyze the email information provided:
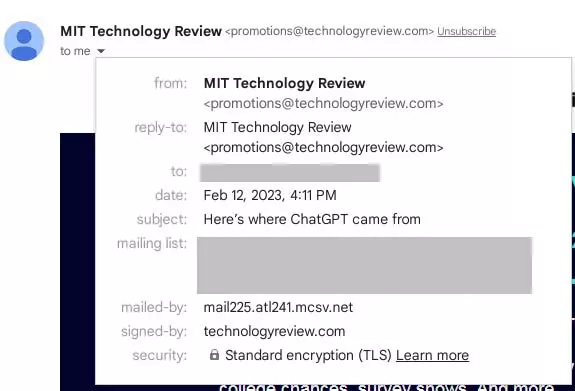
This section can help identify a legitimate email from a phishing email. In our scenario, after conducting your preliminary analysis, you realize that although the public name is Customer Support ABZ Bank, just as all emails from the bank have, the email address in the email information box uses the public Gmail domain. This is a huge red flag and a high chance it is a phishing email!
What Steps Can You Take?
a. Do not take any action in such an email such as clicking links or downloading or opening documents
b. Open another email from ABZ bank that you can authenticate and confirm its legitimacy. If you have none, log in to your bank's website by clicking a bookmarked link or a link on a browser's web search results. Trigger an action that will result in an email being sent to you such as requesting a transaction statement.
c. Compare the headers of the legitimate email with those of the suspicious email. Chances are the emails' information will not match.
d. Contact your bank's fraud department or customer service and let them know about the email. Delete the suspicious email. You can also alert your email provider by reporting the email to them. In Google's Gmail, click on the three vertical dots on the right side of the email and select block, report spam, and report phishing. You can do all three!
STEP 1
STEP 2
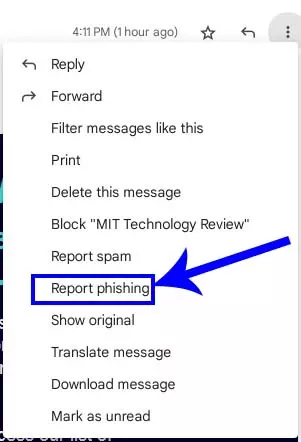
Please note that the above emails from MIT Technology Review are legitimate and I am using them for demonstration purposes. I am always expecting emails from this sender.
3. Email Address Does Not Match The Content
Another email from ABZ Bank is in your inbox and is claiming that your account has been flagged by security agencies and is currently on hold. There is a big blue button that reads, "Fix Account Now" and a phone number with the label, "Call to Contact Customer Service".
Most people will panic and click the button or hastily call the number. There is a good reason to act fast. After all, it is your hard-earned money at risk! But you are not like most people. You go to the email's headers to confirm the originating email address. You realize that the sender's email address is . This is a huge red flag and you sense that this is a scam. Ask yourself, how is ABZ Bank using a mixed-up and funny-looking email to send red alerts?
What Steps Can You Take?
Contact the organization that the email is alleged to come from such as your bank, workplace, government institutions, eCommerce businesses, and others, and let them know of the attempted fraud. Ignore and delete the email. It is important to use the normal login routes to access the accounts such as bookmarked webpages or results from a browser's web search results and evaluate if everything is in order. This step is just to give you peace of mind that your account has not been tampered with.
4. Email Domain Name Does Not Match (Cybersquatting - Typosquatting)
Not all attackers use public domains such as Google's Gmail, Microsoft's Live, or even Yahoo. There are those with the dedication to make it appear more legitimate. An attacker can develop an interest in your bank, ABZ Bank, not as a client but as a phishing email attacker. But this is not your normal-day scammer (or hacker) as he or she has got tools and skills up his or her sleeve.
STEP 1
First, these attackers conduct extensive research on organizations whose clients fit certain criteria such as consistent complaints to customer support, loads of promotional emails from organization to customer, and more.
STEP 2
The attackers then get a closely matching domain to that of the legitimate organization, commonly known as cybersquatting. For instance, an organization, MedLink Insurance (hypothetical) can have a domain and a website . An attacker goes ahead and creates the domain, . Have you spotted the difference? The attackers replaced the m in the legitimate domain with the letters rn in the fake domain hoping to trick users into clicking the fake link.
STEP 3
Now the attackers have the domain. Next, they need to get a website for this fake domain and this is where it gets interesting. Attackers use their IT expertise and free tools such as HTTrack to clone legitimate websites and copy them to the faked domain created earlier. As a user, you would not tell the difference in terms of colors, fonts used, images, and even links. However, website cloning software DOES NOT clone backend scripts hence some operations such as login CANNOT work.
STEP 4
Once the cloned website is active, the attackers will begin sending out phishing emails to clients of legitimate organizations in the hopes that some will fall for the scam (or hack). The emails sent have the same design as those from the legitimate domain; however, links contained in such emails are redirected to the fake domain.
How to Protect Yourself From Phishing Attacks Associated With Cybersquatting
-
Pay close attention to an email's domain name. Taking a second or two to verify the legitimacy of the domain can help protect your data. Watch out for any misspellings in the domain (missing or extra letters and characters).
-
Avoid clicking any links in an email until you can verify their legitimacy and authenticity and be sure of the source and sender
-
Bookmark the websites you consider critical such as your bank's and e-commerce websites. Navigate to these sites rather than clicking links in an email directing you to the sites. Bookmarking also helps prevent you from typing your email into a browser's URL box. A single typo, such as foogle.com other than google.com might lead you to a URL-hijacked, fake domain.
-
Fake domains rarely (try never) appear in search engines' results. Therefore, you can search for an organization and click on a result from a browser's web results. However, be aware that fake domains can create ads that appear at the top of search engines. Therefore be skeptical about such domains.
Typosquatting attacks are dangerous as they can easily be executed and people become victims easily. These attacks are not only used in email phishing attacks but can be part of larger and more sophisticated attacks on organizations and even governmental departments.
How to Spot a Phishing Email From The Message Body
Analyzing the source address and the domain of the sender is a great way to spot a phishing email. There are other ways to raise your suspicion about an email. Please note that these steps help raise your suspicion level and are in no way a direct qualification to ignore an email. However, when a red flag is raised, DO NOT interact any further with the email (DO NOT click links and buttons, reply to the email, or follow other steps that may be given in the email such as making a phone call) rather do some research about the email with information from the information box, as we have described above to validate its authenticity.
1. Grammatical Mistakes in the Email Message
If an email has grammatical errors such as misspelled words, tenses mix-ups, and misused pronouns- he, she, it, they- then you should proceed with caution. Phishing scammers do not entirely use English as their first spoken language hence the existence of such errors. We do not say that all emails with grammatical errors are phishing emails and scams, we emphasize looking closely and investigating if the email is legitimate. To do so, check the sender's address and sender's domain in the email's information box, as we have explained in the above section. If you spot a red flag, you should be certain you are dealing with a phishing email and there is a scammer at the end of the email.
2. Email Has a Tone of Urgency
Look at the email below:
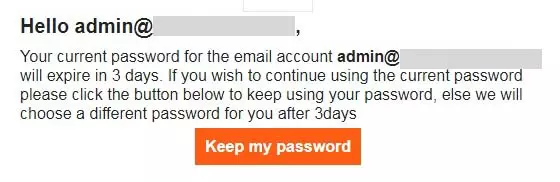
The email instructs the receiver to click the big button 'Keep My Password' or the password to the email address will be changed automatically in 3 days. The email above has a tone of urgency (3 days) and 'suggests' immediate action (Click the button) or retaliatory steps will be taken (password changed automatically).
Phising emails may have a soft threat and in some instances, a hard threat such as blackmail. As you can see, this category of phishing emails often have the 'act-now-or-else' tone.
At that moment you are panicking, that's when you are likely to click a link, reply to an email, or call a number provided within the email. That panic was the whole idea that the attackers and scammers had. They aimed to instill fear and panic in you. Phishing scammers know that the longer you take to think about something, the clearer it becomes. And so, just like the above email, you get 10 minutes or even a few hours to complete the action.
Once you click a link in the phishing email, chances are you'll be redirected to prohibited websites or URL-hijacked websites (see above on Typosquatting) or the links will download harmful malware, adware, and ransomware into your devices for the complex hacks. This action will make you a victim of a painful journey characterized by identity theft, blackmail, and fraud, among others.
If you make a phone call that is included in the email's details, chances are you are about to be scammed, be part of a social engineering attack, or simply conned. Large phishing scammers use robocalls to first answer your call and give you further instructions such as 'Press 1 to talk to a Customer Service agent'. It is then forwarded to a real person once you take an action such as pressing the number. That is when the scam starts on free product trials, fake investment opportunities, fake wins from a competition, 'guaranteed' loans or credit, business insider secrets, and even the more common tech support and refund scams.
3. Generic Greetings
If you have an account with an organization or website, they already have your information, such as names, to personalize an email. If an email starts with Dear Sir/Madam, chances are that it is a phishing email and might not originate from your bank or local pet store. Such emails are common with salespeople, promoters, and of course, email scammers. Organizations and institutions such as banks, e-commerce sites, and even government departments will refer to you in the email by your name and not a generalized 'Dear Sir/Madam'.
How To Protect Yourself from Email Phishing
-
Before you click a link or call a number in an email, visually analyze the email to spot suspicious elements such as grammatical errors.
-
Always verify that the sender and source are authentic. These details are contained in the information box of an email.
-
If you did not expect the email, do not be quick to act on it. An email from a friend or family member might not be safe. If your friend's device is infected with a virus, a bot could scan the device, fetch all email addresses, and send out emails. If a suspicious email appears from a friend or family member, call that person to confirm that they indeed sent the email.
-
Treat email attachments with caution. Do not open email attachments such as documents and other files. If you feel that the email could be legitimate but still suspicious, go to your organization's website through your bookmarks or via a search engine search. Even safer, look for a physical document such as a bill or statement and contact the organization.
-
Delete all suspicious emails confirmed as phishing emails. Once you are sure that an email is not legitimate, delete it immediately.
-
Always report suspicious emails to organizations and institutions. Reporting such emails through an organization's select channel helps the organization recognize the threat and take precautionary measures, which may include sending out alerts.
-
Set up email filters. Most email providers allow custom filters on emails.
-
Do not give in to pressure more so to emails with a tone of urgency. Always do some research outside the email to confirm the legitimacy of the email.
-
If you did not expect an email, it's probably a phishing email. Apart from emails from subscriptions and newsletters, any other email should not be expected. If you are not part of an investment group, an email offering free financial and investment advice should be suspicious. If you did not order a package or shopped online, emails claiming to have your package should be suspicious.
-
Always remember if it sounds too good and easy, it is probably fake. Emails with promises of huge investment opportunities with high gains, insider business information, 'guaranteed' credit and loan services, tax refunds with no paperwork, and even vacation prizes from random competitions should be suspicious.